AWS SSO with Auth0 for Free
For several years, I have been using AWS with my personal account, notably for projects presented in my previous blog posts such as creating my blog or also the serverless redirector URL always aiming to push costs towards zero.
In this blog post, we will see how to set up AWS IAM Identity Center (formerly AWS SSO) with Auth0 for free using your federated authentication through Auth0 (in my case, via Google).
TLTR: The GitHub repository with the readme

Prerequisites
To understand this post, you should:
- Know Terraform and notably deploy on AWS via Terraform
To reproduce the example in this blog, you need:
- To have an AWS account and credentials
- To have an Auth0 tenant and credentials
- To deploy the infrastructure on AWS via Terraform
Info
The solution uses Terraform and automates as many steps as possible. This blog post does not aim to describe the manual actions to perform on AWS or Auth0 in detail.
The initial challenges
Like most people using a personal AWS account, you quickly end up with an IAM user knowing that there is only one account to log into. However, I encountered several issues over time:
- An IAM user with username and password in addition to my other credentials
- The use of Access and Private Keys across multiple workstations must be shared securely but this is not always the case. I won’t even mention the challenges involved in rotating keys.
- I wanted to create several AWS accounts to separate my projects. An SSO configuration simplifies access management by automating the “assume role” between multiple AWS accounts.
So I wanted to set up AWS IAM Identity Center (formerly AWS SSO) through my Google email address to centralize and simplify authentication on my side. After some research, it quickly appears that the integration is made for Google Workspace. Bad news because Google Workspace is a paid enterprise-oriented offer, which is a bit unfortunate for “Mr. Everyone,” who only has a personal email address.

How to set up AWS IAM Identity Center (formerly AWS SSO) while using Google’s federated authentication?
The Auth0 solution
After some research, Auth0 seemed to be the perfect candidate because it allowed on one side to authenticate via Social Connections including Google (Gmail in my case) but also many others like Microsoft, GitHub, etc. And on the other side to set up AWS IAM Identity Center (formerly AWS SSO) with Auth0 and for free!
The workflow for connecting to the AWS account is as follows:
graph LR;
A[Google/Gmail authentication] -->|Oauth 2.0| B(Auth0)
B --> |SAML 2.0| C(AWS account)
Auth0 side and pricing?
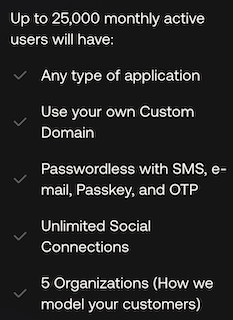
On this side, we have plenty of room since the Free plan includes 25,000 monthly active users which is more than enough for personal use or even for a startup scale.
Beyond that, the Auth0 pricing on the Free plan offers quite a few interesting features:
Deploying the solution
I implemented the solution through Terraform to automate deployment as much as possible and you can dive into the GitHub repository for the more curious among you.
Solution prerequisites
To use the solution, you will need:
- An AWS account with a user having all permissions on
identitystoreat least and credentials usable by Terraform. You can rely on the AWS provider documentation - An Auth0 tenant with a user having enough permissions to manage applications and users in the tenant. You must also generate a token for this user, based on the Auth0 provider documentation (based on the Auth0 provider documentation).
Finally, before starting the next steps, do a GIT clone of the GitHub repository
ClickOps
The AWS API for AWS IAM Identity Center (formerly AWS SSO) is (very) limited and does not allow creating or retrieving certain elements. We therefore need to perform some manual actions which are:
- Go to your AWS account management and select the primary region you use.
- Go to AWS IAM Identity Center (formerly AWS SSO) and activate it.
- Configure the external identity provider source
- Retrieve the AWS IAM Identity Center Assertion Consumer (ACS) Service URL and place the value in your
terraform.tfvarsvia the variableaws_acs_callback_url. - Do not close the previous AWS page when you are missing information in the
Identity provider metadatasection: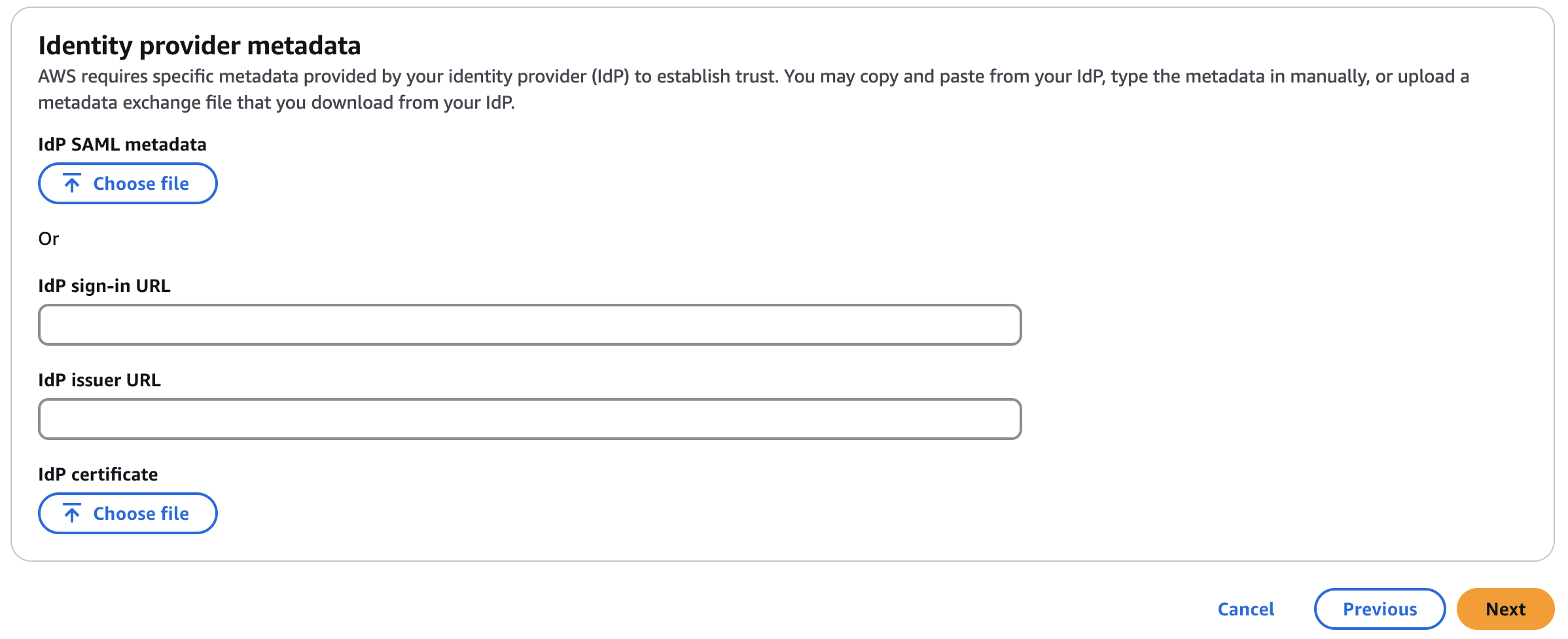
- In your
terraform.tfvarsfile, add values for the variablesregion(the chosen primary AWS region) andauth0_domainwhich represents your Auth0 tenant (e.g., doge.eu.auth0.com).
The AWS page must remain open and will be finalized in the next steps after terraform apply.
Info
At this stage, your terraform.tfvars file must contain the following variables:
aws_acs_callback_urlregionauth0_domain
Creating groups, users, and policies
To create a group, you will need to use the Terraform variable sso_groups in your terraform.tfvars file.
Here is an example of the variable content (keep in mind the variable represents a list of groups):
sso_groups = [
{
name = "DevOps"
description = "The DevOps team",
policy_arns = [
"arn:aws:iam::aws:policy/CloudWatchLogsFullAccess" # Policy must exist in the target account
],
account_ids = [
"123456789012", # AWS account ID
]
members = [
"contact@mehdilaruelle.com",
],
},
]
In the previous example, we have:
- name: which is the group name.
- description: the group description (always good to have one).
- account_ids: the list of account IDs.
- policy_arns: the list of AWS managed policies. There is a limit of 10 policies per group. You can bypass this limit via an inline policy.
- members: a list of your users’ identifiers. You must use the users’ email addresses to authorize their connections.
Warning
AWS managed policies must exist on the AWS account IDs to avoid errors that the policy does not exist. Prefer using an AWS managed policy present on all AWS accounts rather than Customer managed policies.
Final configuration step and result
Once the previous steps are done, you can run a terraform apply. It will give you outputs that we will use
later.
It’s time to finalize the configuration:
- Use the following command
terraform output -raw aws_sso_idp_metadata > /tmp/auth0_metadata.xmlto save the file in/tmp/auth0_metadata.xml - Return to the previously opened AWS page on the external identity provider source
and upload the file in the
Identity provider metadatasection:
- Return to the main page AWS IAM Identity Center (formerly AWS SSO)
and retrieve the
AWS access portal URLon the right section of the page (save it in your bookmarks).
The configuration is finalized. The AWS access portal URL will serve as the login link to your AWS accounts.
Configuration verification
If I take the following example configuration:
sso_groups = [
{
name = "Admin",
description = "The admin group.",
policy_arns = [
"arn:aws:iam::aws:policy/AdministratorAccess"
],
members = [
"contact@mehdilaruelle.com"
],
account_ids = [
"123456789012"
],
},
]
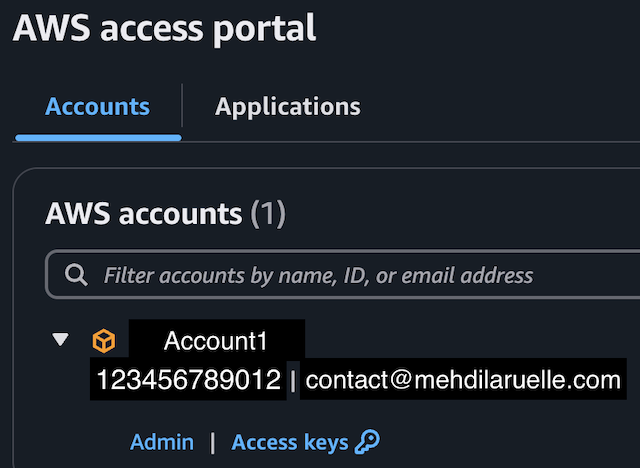
I should be able, with my email address, to connect to only one account: 123456789012 via the Admin permission.
To verify this (with your AWS account), use the AWS access portal URL which should redirect you to an Auth0 page:

In my case, I log in via Google. A second page appears with the list of accounts (in my case, only one account):
 Just click on
Just click on Admin, which will redirect you to your account with the correct rights.
You can configure your AWS CLI with SSO for command line usage.
And what’s next?
The GitHub repository takes into account the variable auth0_connection_name
which takes the name of an Auth0 connection. If this input is provided, users created in AWS IAM Identity Center (formerly AWS SSO) will also be created in Auth0 in the provided Auth0 connection.
Among possible next steps, implementing SCIM (System for Cross-domain Identity Management) could be an improvement idea even though often the feature is paid as it is seen as an enterprise feature.
The repository is under construction; if you have ideas or suggestions for improvement, they are welcome.
Conclusion
We have seen how to implement SSO in AWS through Auth0 and AWS IAM Identity Center (formerly AWS SSO) while using our Social Connections such as Google/Gmail and for free.
Finally, the solution is deployable through the GitHub repository even though some actions remain manual unfortunately due to the lack of API on the AWS side.
AWS Terraform HashiCorp Auth0 SSO Security Automation Identity Center IAM Google
1341 Words
2025-04-24 06:00